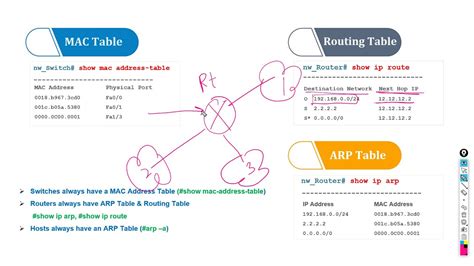
The article ARP Table Management For Security Camera Systems emphasizes the critical role of ARP table management in enhancing the security of surveillance systems. It begins by explaining how effective ARP table management is essential for preventing unauthorized access and ensuring system integrity. The article highlights various challenges associated with maintaining an efficient ARP table, including potential vulnerabilities that could be exploited by attackers. To address these issues, it outlines best practices for enhancing ARP table security, such as regular reviews and implementing access controls. Furthermore, the piece discusses the importance of actively monitoring and analyzing ARP table entries to detect irregularities. In conclusion, it summarizes key takeaways on the significance of ARP table management for safeguarding security camera systems, underscoring that diligent management can significantly mitigate risks.
Understanding The Importance Of ARP Table Management
Effective ARP Table management is crucial for enhancing the security and performance of security camera systems. As these systems rely heavily on data transmission over a network, any inefficiency or vulnerability in the Address Resolution Protocol (ARP) can expose the network to attacks. By understanding the significance of ARP table management, network administrators can protect sensitive data and ensure that surveillance footage remains secure and accessible.
One of the primary reasons for handling ARP Table management is to reduce the risk of ARP spoofing, a method where an attacker sends false ARP messages onto the network. This can lead to man-in-the-middle attacks, where the attacker intercepts and potentially alters the data being sent between devices. Properly managing the ARP Table can help to identify and mitigate these risks before they become significant issues.
Key Reasons For Managing ARP Tables
- Preventing ARP spoofing attacks
- Enhancing network performance and efficiency
- Minimizing network downtime and disruptions
- Ensuring data integrity and security
- Facilitating easier network troubleshooting
- Maintaining accurate network mappings
Furthermore, regular monitoring and maintenance of the ARP Table contribute to better network visibility and control. With the growing sophistication of cyber threats, a well-managed ARP table aids in quickly identifying unauthorized devices and blocking any potential security breaches. In conclusion, prioritizing ARP Table management not only aids in preserving the integrity of security camera systems but also protects the overall network environment. Proper management entails the combination of efficient strategies and continuous monitoring to safeguard sensitive data against ever-evolving threats.
Challenges In Efficient ARP Table Management
Efficient management of the ARP Table is crucial for maintaining network performance and security, especially in systems such as security cameras. The Address Resolution Protocol (ARP) facilitates the mapping of IP addresses to MAC addresses, but managing this process isn’t without its difficulties. As camera systems become progressively complex and widespread, ensuring the integrity of the ARP Table becomes even more challenging.
Common Issues Faced In ARP Table Management
- ARP Spoofing Attacks
- Table Overflow due to excessive entries
- Stale Entries causing connectivity issues
- Inconsistent Entries leading to communication failures
- Insufficient monitoring and alerting mechanisms
One of the primary challenges is the vulnerability to ARP spoofing attacks, where a malicious actor sends falsified ARP messages over a local area network. This can lead to unauthorized access or denial of service to legitimate devices. In addition to security threats, the ARP Table can become overwhelmed with excessive entries, leading to a phenomenon known as table overflow, which can drastically hinder performance.
Another common issue is stale entries. Over time, entries in the ARP Table can become outdated if devices are removed or IP addresses change without proper updating. This can lead to connectivity issues, making it difficult for surveillance cameras to communicate efficiently. Furthermore, inconsistent entries can result from network changes or misconfigurations, causing communication failures between devices.
Lastly, a lack of sufficient monitoring and alerting systems exacerbates these challenges. Without proper tools to analyze and manage the ARP Table, recognizing and addressing issues in real time becomes nearly impossible. Therefore, organizations must implement robust monitoring strategies to ensure that their ARP management processes remain effective in supporting security camera systems.
Implementing Best Practices For ARP Table Security
To enhance security for networked systems like security camera setups, it is critical to implement stringent measures for the ARP Table. The Address Resolution Protocol (ARP) is essential for mapping IP addresses to MAC addresses, but its vulnerabilities can be exploited by malicious actors. Strong practices are key in safeguarding these tables against various types of ARP spoofing attacks that can compromise entire network systems. Therefore, understanding and implementing effective strategies to protect the ARP Table will help maintain the integrity of your security infrastructure.
Effective Strategies For ARP Table Security:
- Regularly audit ARP entries to identify any unauthorized modifications.
- Implement static ARP entries for critical devices to prevent spoofing.
- Use ARP monitoring tools to detect unusual activity.
- Segment the network to limit exposure of sensitive devices.
- Educate staff on the risks of ARP vulnerabilities and preventative measures.
- Utilize packet filtering firewalls to block suspicious ARP traffic.
- Establish a responsive incident response policy for ARP-related threats.
Creating a proactive approach to the security of the ARP Table involves not only implementing these strategies but also actively monitoring the situation. Regular risk assessments can help identify potential vulnerabilities in your network which may be exploited via ARP attacks. By continuously evaluating your security tactics, you can adapt to the evolving landscape of cyber threats, ensuring your security systems remain secure. Furthermore, maintaining an updated protocol for handling security breaches is essential for quick recovery and minimizing damage.
In addition, leveraging tools that provide real-time alerts on changes to the ARP Table is an effective way to ensure integrity. Tools that facilitate the logging of ARP requests and responses can give insight into potentially malicious activity. By creating a layered security strategy that integrates these monitoring solutions with training and awareness programs, organizations can significantly reduce the likelihood of successful ARP attacks against their critical systems. Always remember that the goal is to proactively safeguard your network environment, making it impervious to manipulation.
Monitoring And Analyzing ARP Table Entries
Monitoring and analyzing the ARP Table is vital for security camera systems as it directly impacts network performance and security. The Address Resolution Protocol (ARP) table maintains a mapping between IP addresses and MAC addresses, making it a crucial component for network communication. Regular analysis of this table can help identify potential threats, such as ARP spoofing, and ensure that devices communicate smoothly without unauthorized interference.
Understanding how to effectively analyze entries within your ARP Table can assist in maintaining a secure network. Often, networks can become cluttered with obsolete or incorrect entries, which may result in performance issues. By routinely monitoring the ARP table, network administrators can remove outdated entries and replace them with correct information, thus enhancing the overall security of the security camera systems.
Effective management of the ARP table can significantly reduce vulnerabilities while improving the network’s reliability and performance.
Steps To Analyze ARP Table Entries
- Access the ARP table using terminal or command prompt commands.
- Identify current IP-to-MAC address mappings listed in the table.
- Check for any suspicious or unknown MAC addresses.
- Look for duplicate entries that may indicate a problem.
- Remove obsolete entries that are no longer in use.
- Document any changes made to the table for future reference.
- Schedule regular audits of the ARP table to maintain its integrity.
Once the analysis of the ARP Table is complete, the next step is to implement the best practices for maintaining its security and efficiency. It’s essential to ensure continuous monitoring, applying updates when necessary, and proactively responding to any anomalies found during your analysis. Ensuring that the ARP table reflects the current state of the network is pivotal in mitigating risks, especially in environments where security cameras are deployed.
Conclusion: Key Takeaways On ARP Table Management
Effective management of the ARP Table is crucial for maintaining the security and performance of security camera systems. As technology evolves, so do the tactics used by cyber threats to exploit vulnerabilities. Thus, comprehending the importance of the ARP Table allows network administrators to take proactive measures in safeguarding their systems against potential attacks.
In addition to being proactive, organizations must also remain vigilant in monitoring ARP entries regularly. This continuous oversight ensures that any unauthorized devices attempting to gain access to the network can be identified and addressed promptly. It is equally important to regularly audit and update the ARP Table to ensure that it reflects the current state of the network.
Essential Tips For Effective ARP Management
- Regularly verify ARP entries to identify unauthorized devices.
- Implement static ARP entries for critical devices.
- Utilize ARP monitoring tools for real-time tracking.
- Segregate networks to limit ARP broadcast traffic.
- Educate staff about ARP spoofing and its implications.
- Periodically refresh the ARP cache to eliminate stale entries.
To summarize, efficient ARP Table management involves not only understanding its significance but also executing best practices that enhance network resilience. By prioritizing security measures and staying informed about industry advancements, organizations can protect their security camera systems from emerging threats while ensuring optimal functionality.