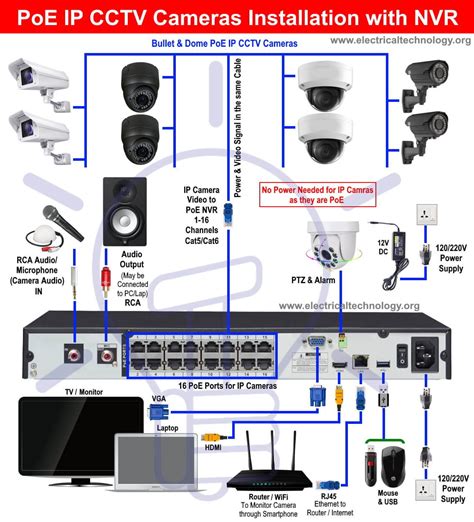
ARP tables play a crucial role in ensuring reliable connectivity for security cameras within a network. This article delves into the importance of ARP tables, explaining how they function in various network environments. Properly configured ARP tables facilitate efficient communication between devices, enhancing overall network performance. The article also addresses common issues that may arise with ARP tables, along with effective resolutions to maintain seamless connectivity. Additionally, readers will find useful best practices for maintaining ARP tables, which is essential for optimizing security camera systems. By understanding ARP tables, individuals can significantly improve the functionality and security of their surveillance networks.
The Importance Of ARP Tables For Security Camera Connectivity
Understanding ARP Tables is crucial for maintaining seamless connectivity between security cameras and network devices. ARP (Address Resolution Protocol) essentially maps IP addresses to MAC (Media Access Control) addresses, enabling devices to communicate effectively on a local network. For security cameras, a solid connection is essential as it ensures continuous data transmission, reporting, and monitoring. If ARP tables are improperly configured or monitored, it can lead to connectivity issues that might disrupt the camera’s functionality.
When security cameras are installed within a network, they rely on ARP Tables to identify and connect with other devices, such as recording servers or viewing stations. Each device conducts a lookup in the ARP table to determine the corresponding MAC address linked to an IP address. This process is vital for establishing and maintaining a reliable connection, especially when multiple cameras and devices are involved in a complex security system.
Key Reasons To Understand ARP Tables
- Facilitates effective device communication.
- Reduces the chance of IP conflicts.
- Enhances network troubleshooting efforts.
- Assists in optimizing bandwidth usage.
- Improves overall network security.
- Ensures quicker response times for security feeds.
- Helps in monitoring unauthorized access points.
By regularly reviewing and updating ARP Tables, network administrators can ensure that security cameras maintain optimal connectivity. This practice not only helps minimize downtime but also plays a crucial role in securing the network against potential threats. In environments where security is a top priority, understanding and utilizing ARP tables effectively becomes indispensable for keeping the surveillance system robust and reliable.
How ARP Tables Work In Network Environments
The functioning of ARP Tables is crucial for ensuring effective communication within network environments. When a device wants to communicate with another device on the same local network, it must know the corresponding MAC (Media Access Control) address to establish a proper link at the Ethernet level. In this context, the Address Resolution Protocol (ARP) acts as the intermediary that helps translate IP addresses into MAC addresses, allowing seamless networking without the need for manual input.
Understanding how ARP Tables are constructed and managed is essential for optimizing network performance. Each time a device resolves an IP address to a MAC address, it updates its ARP table with the newly acquired information. This table serves as a local cache for storing mappings, which minimizes the need for repeated lookups and significantly speeds up network communications. Over time, the data in these tables may age out and require updates to ensure accuracy.
Steps Involved In ARP Table Functionality
- The device broadcasts an ARP request to the local network, seeking the MAC address associated with a specific IP address.
- All devices on the network receive the ARP request; the device with the matching IP address responds with its MAC address.
- The requesting device receives the MAC address and stores this information in its ARP Table.
- When the device needs to send data again to the same IP address, it checks its ARP table first for the corresponding MAC address.
- If the MAC address is not found, the device repeats the ARP request to populate the table again.
- ARP entries have a specific timeout period; once expired, they are removed from the ARP Table to maintain current data.
- Proper management and regular updates of ARP Tables are necessary to prevent connectivity issues within the network.
Ultimately, simplifying the migration between different levels of network communication relies heavily on ARP Tables. Without this critical functionality, devices would struggle to locate one another, resulting in delayed communications. Furthermore, understanding the flow and behavior of ARP tables can help network administrators troubleshoot connectivity issues more effectively, contributing to more robust network performance overall.
Benefits Of Properly Configured ARP Tables
Configuring ARP Tables properly is essential for maintaining an efficient and secure network environment, particularly in setups involving security cameras. This configuration plays a pivotal role in ensuring that devices can communicate with each other seamlessly. Without a well-structured ARP Table, devices may face delays in connectivity or, worse, improper routing of data, which can compromise the integrity of surveillance systems.
Moreover, optimized ARP Tables contribute significantly to reducing network congestion. By eliminating unnecessary broadcast traffic that occurs when devices are trying to locate one another, smooth and efficient communication is achieved. This optimization not only enhances the performance of security camera connectivity but also improves the overall health of the network.
Advantages Of Optimizing ARP Tables
- Improved network performance through reduced broadcasts.
- Enhanced security by minimizing ARP spoofing risks.
- Faster device communication, leading to quicker video feed transmission.
- Lower latency, particularly important for real-time surveillance applications.
- Easier management of connected devices.
- Stability in network performance as devices communicate more accurately.
In summary, the benefits of properly configured ARP Tables extend beyond simple connectivity. They encompass significant improvements in security, data integrity, and operational efficiency. Implementing best practices in the configuration and management of these tables is not just advisable but necessary for robust network functionality, particularly in environments reliant on security cameras and other critical devices.
Common Issues With ARP Tables And Their Resolutions
One of the most common issues with ARP Tables is the presence of stale entries. Stale entries occur when devices that once communicated over the network no longer exist or have changed their IP addresses. This can lead to significant connectivity problems, particularly for security cameras that rely on accurate address resolution for communication. These entries can cause data frames to be sent to the wrong devices, which not only hampers performance but can also create vulnerabilities that could be exploited by malicious entities.
The second major issue arises from ARP spoofing or poisoning. In this scenario, an attacker sends malicious ARP messages over the network, thus linking their MAC address to the IP address of another device, which can facilitate man-in-the-middle attacks. As a result, the unsuspecting devices continue to send frames to the attacker instead of the intended recipient, compromising the integrity and security of the data being transmitted. Organizations must take proactive measures to detect and mitigate this type of attack.
Steps To Troubleshoot ARP Table Problems
- Verify the integrity of the ARP entries using the ‘arp -a’ command.
- Clear stale entries to refresh the ARP Tables.
- Ensure that all devices have updated software and firmware to prevent vulnerabilities.
- Implement dynamic ARP inspection to combat ARP spoofing.
- Monitor network traffic for unauthorized ARP requests and responses.
- Regularly update security policies related to network device configurations.
- Educate users on the importance of network security practices.
Finally, another prevalent issue is IP address conflicts, which may arise when two devices are assigned the same IP address in the ARP Tables. This leads to unpredictable behavior on the network, making it impossible for devices to communicate effectively. Resolving these conflicts requires careful management of the IP address allocation process, especially in environments with numerous devices, such as those used for security camera systems.
In summary, understanding the common issues related to ARP Tables is crucial for maintaining seamless connectivity and security in network environments. Timely resolution of stale entries, prevention of ARP spoofing, and careful management of IP address assignments can significantly enhance the reliability of your security camera systems. By implementing best practices and troubleshooting methods, network administrators can ensure a robust and secure networking environment.
Best Practices For Maintaining ARP Tables
Maintaining ARP tables is crucial for ensuring efficient communication within a network, especially in environments utilizing security cameras. An effective ARP table management strategy not only enhances performance but also bolsters the security of networked devices. By implementing best practices, network administrators can prevent common issues like IP conflicts and enhance overall connectivity reliability.
Regularly clearing and updating ARP tables can prevent outdated information from causing network failures. It’s vital to schedule periodic reviews of ARP entries to verify their accuracy and relevance. As devices are added or removed from the network, ensuring that the ARP table reflects these changes can minimize connectivity problems and improve response times for all network devices.
Essential Tips For Effective ARP Table Management
- Regularly clear outdated ARP entries to maintain table integrity.
- Implement static ARP entries for critical devices to improve reliability.
- Monitor ARP traffic to identify unusual patterns that could indicate issues.
- Document any changes made to the ARP table for future reference.
- Establish a routine for reviewing and updating ARP settings.
- Utilize network management tools to automate ARP table maintenance.
Network policies must also address the security of ARP tables. Ensuring that only authenticated devices can communicate on the network is key to preventing ARP spoofing attacks. Utilizing techniques like dynamic ARP inspection or port security can help safeguard the network by verifying that ARP packets originate from legitimate sources, therefore enhancing the security of sensitive devices like security cameras.
In conclusion, effective management of ARP tables is a fundamental aspect of maintaining a secure and efficient network. By following best practices such as regular updates, monitoring traffic, and securing devices, network administrators can significantly mitigate risks associated with improper ARP management. A well-maintained ARP table not only supports optimal device communication but also fortifies the network against potential threats.